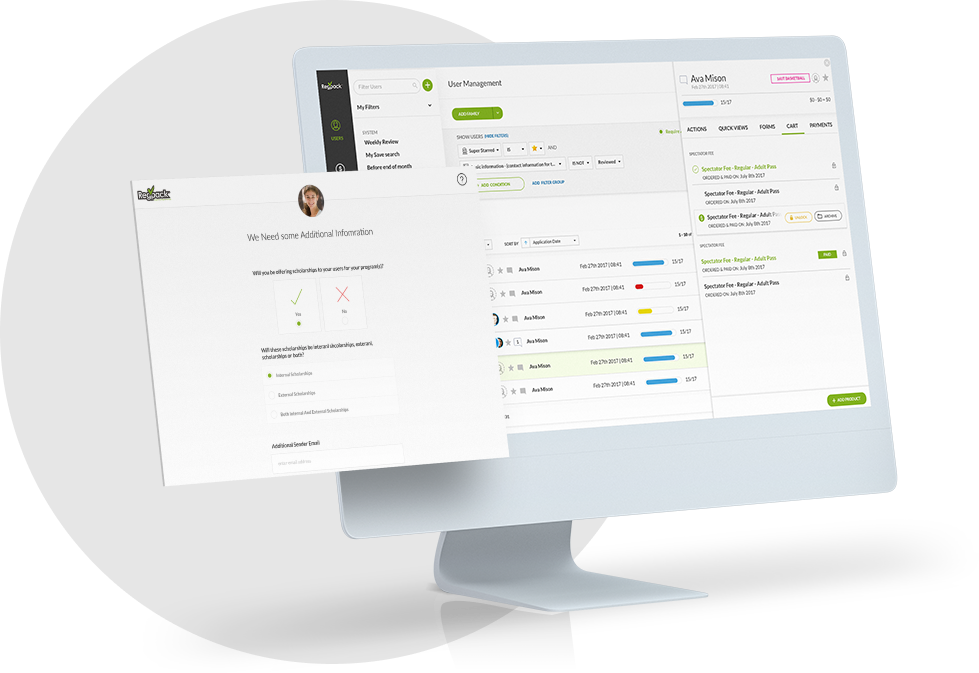
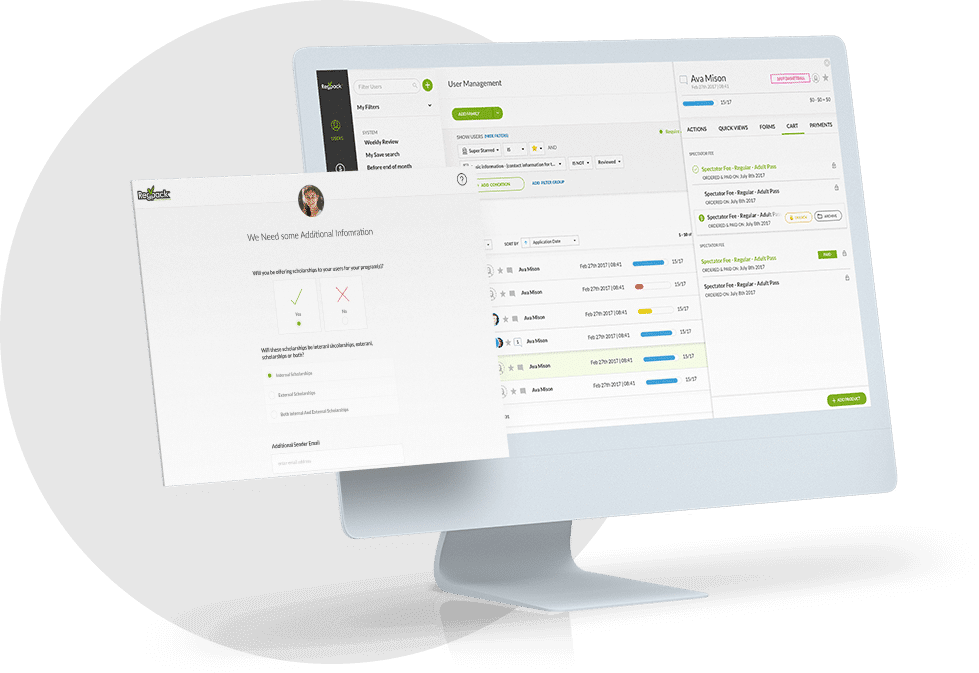
In 2022, your customers probably don’t think twice before giving you their credit card information to make a payment.
That trust is well-founded thanks to the Payment Card Industry Data Security Standard (PCI DSS), which sets strict requirements for how merchants need to handle credit card information and process card transactions.
But what about bank transactions, otherwise known as ACH payments? After all, bank account numbers are even more at-risk than credit card numbers, since they stay the same year after year.
Thankfully, Nacha, the governing body for the ACH network, has implemented its own set of ACH security rules that should be followed by any network participants.
Merchants who accept ACH should be aware of these rules in order to remain in good standing with Nacha, avoid fines, and continue processing payments safely and effectively.
In this article, we’ll walk you through what merchants need to know to stay in compliance with ACH security rules.
Jump to section:
Nacha Security Guidelines for ACH Transactions
How Nacha Enforces Security Standards
Nacha Security Guidelines for ACH Transactions
Nacha (formerly the National Automated Clearing House Association, or NACHA), governs the ACH network.
It requires all merchants (and third-party processors like Regpack) who run ACH transactions to meet certain security standards in order to protect sensitive consumer data.
Those guidelines include:
- Securing protected information
- Securing transmissions channels
- Validating routing numbers
- Implementing identity verification
- Detecting fraud
- Creating a strong written security policy
We’ll look at each requirement in greater detail below.
Securing Protected Information
First, merchants and other payment processors must protect sensitive customer information.
According to Nacha’s operating rules, protected information is defined as:
“The non-public personal information, including financial information of a natural person used to create, or contained within, an entry and any related addenda record.”
What does this mean in plain terms? Essentially, you as the merchant areresponsible forprotecting any identifying information that is used to create an ACH file, such as:
- Bank account number
- Social security number
- Driver’s license number
Here’s what else that entails.
Securing Transmission Channels
As you might expect, if private information is protected, then the transmission of that information should also be secure.
Transferring sensitive data over the internet has become the preferred method of communication for most vendors and merchants, but using unsecured networks comes with its own level of risk.
When customers fill out an ACH form on their home computer or mobile device, they’re sending that information over an unsecured network.
They’re trusting you to employ the proper security procedures so that their sensitive data like their financial information, address, and full name are protected from prying eyes.
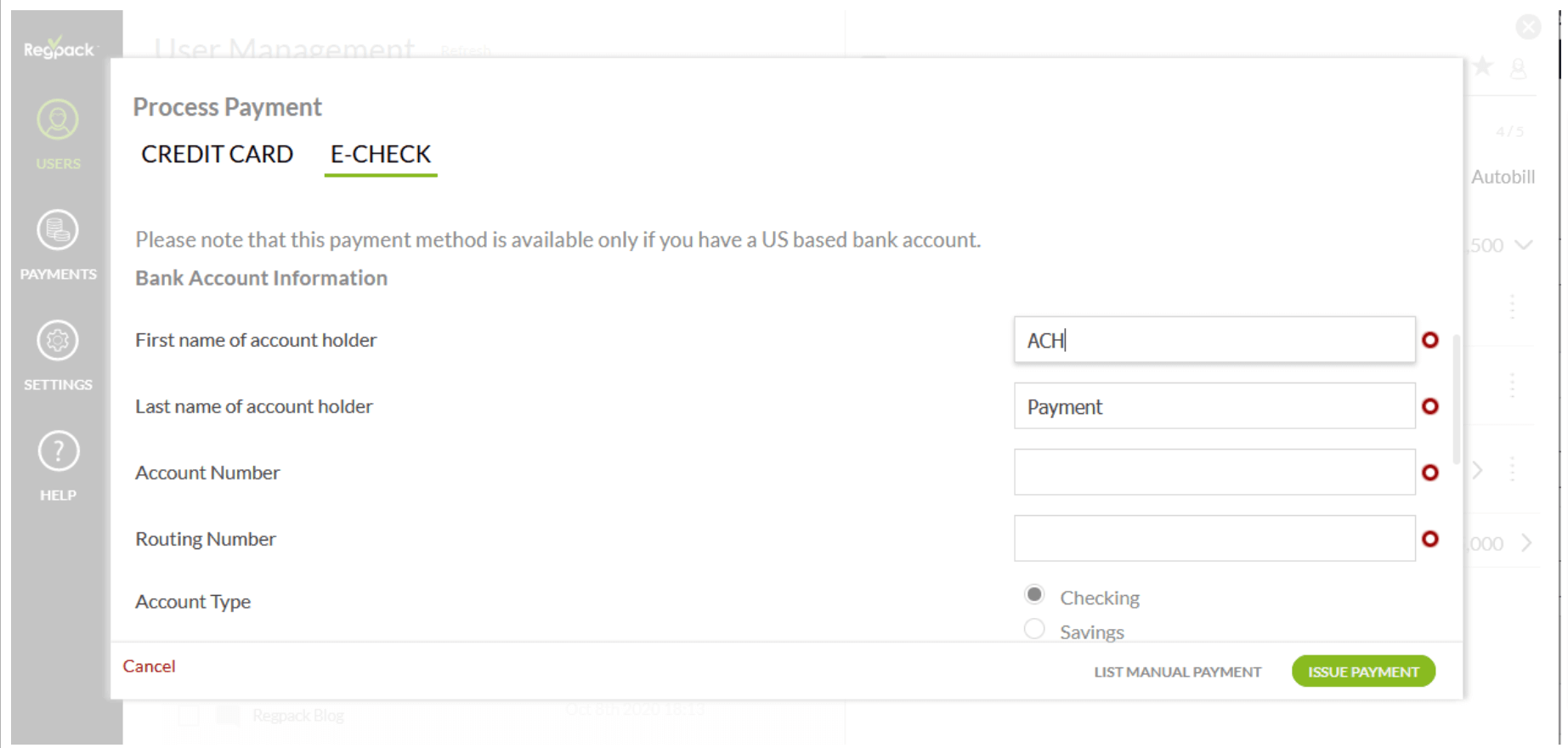
Source: Regpack
If you accept ACH forms online (as most merchants who accept ACH do), it’s important to implement “commercially reasonable” encryption technology and firewalls to safeguard your customers’ private information.
Using insecure web forms or taking sensitive information via email is not acceptable.
To collect protected information on your website, you’ll need a security certificate (SSL) in place, which will turn your page URLs from “http” into “https.”
That extra “s” signifies to visitors that your connection is secure and encrypted, and any information they share with the website should be safe from prying eyes.
If you want to send or receive protected ACH information via email, you’ll need an email with end-to-end encryption.
As Benjamin Brandall writes for Zapier:
“End-to-end encryption can help both individuals and businesses keep their information secret: Unencrypted emails were to blame for at least four major breaches of the past few years, leaking millions of emails and causing millions of dollars of avoidable damage.”
Merchants who need to communicate sensitive customer data over email should invest in an email encryption service such as ProtonMail or Mailfence.
And if you use a third-party software solution for accepting ACH payments, make sure the company you use implements secure encryption methods to protect your customers’ privacy and remain in compliance.
For example, Regpack is PCI-2 compliant and uses both disc-level encryption and the best-in-class WAF (Web Application Firewall) to filter all possible database attacks at the transmission level.
Our secure software lets you collect funds simply and securely, directly from a custom form on your own website.
Validating Routing Numbers
Nacha also requires all merchants (called “Originators”) to validate the routing numbers they enter into the ACH network. This precaution helps guard against both human error and fraudulent behavior.
To validate your customers’ routing numbers, you (or your third-party provider) should check the routing number against a database of valid ones.
If the number doesn’t match a known bank, the ACH transaction should be rejected until the error is fixed.
Implementing Identity Verification
To process an ACH transaction online or over the phone, the only information that’s needed is the customer’s:
- Name
- Address
- Bank routing number
- Bank account number
Unfortunately, this information is easy to come by, either by stealing a paper check or through a bit of detective work.
If a scammer can get their victim’s bank account number and they know which bank holds the account, they can easily find the other information needed to initiate a fraudulent ACH payment using the victim’s information.
Because of how potentially easy it could be to commit ACH fraud, Nacha’s rules for customer identity verification online and over the phone are more strict than the PCI rules governing credit card fraud.
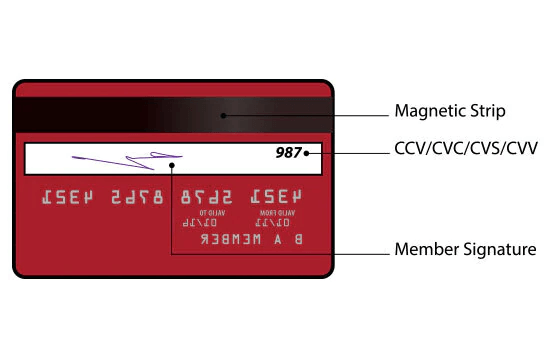
Source: IDFC FIRST Bank
After all, ACH transactions don’t have the safeguards credit cards have in place, such as CVV2 codes to verify the cardholder has the card in their possession, or a database of stolen credit cards to check against.
For ACH transactions, Nacha requires that the merchant use “commercially reasonable” methods to verify the customer’s identity before processing the payment—whether that payment is authorized over the phone or online.
Let’s look at what such commercially reasonable actions might include.
ACH Micro-Transaction Verification
With this method, the merchant tests the account by making 1-2 small deposits (usually under a dollar) in the new customer’s bank account, then withdrawing them shortly afterward.
The customer must then confirm the amounts that were deposited and withdrawn.
This method is an extra obstacle to scammers because it helps verify that the customer has access to their account statements and/or mobile banking dashboard.
ACH Prenotification/Prenote
A prenotification is similar to a micro-deposit, except the customer doesn’t need to take any action to verify the amount—and you don’t need to use real funds to complete the test.
Prenotes work by sending a zero-dollar ACH credit to the customer’s bank account. If the receiving bank doesn’t send you an ACH Return or Notification of Change (NOC), the prenote is successful, and you can begin processing real transactions.
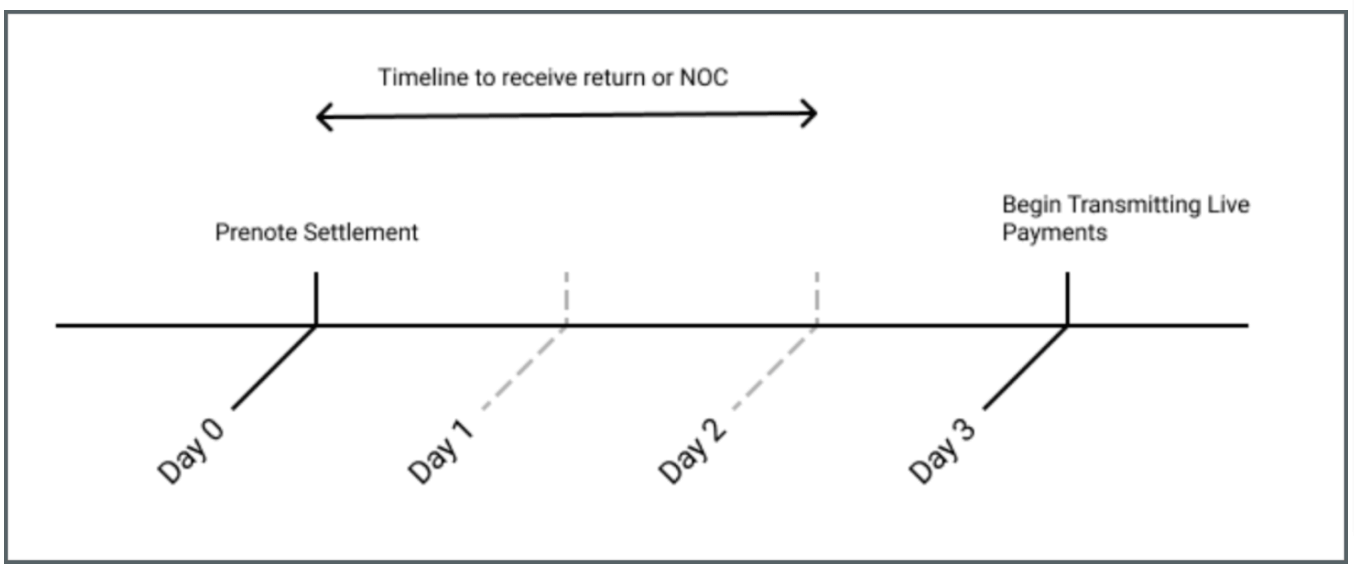
Source: Modern Treasury
As you can see in the figure, the ACH prenotification process can take up to three days.
Third-Party Identity Verification Services
Finally, you can use a third-party service to validate customer identities for you.
Nacha provides a list of vendors that offer these services either alongside ACH transaction services or independently.
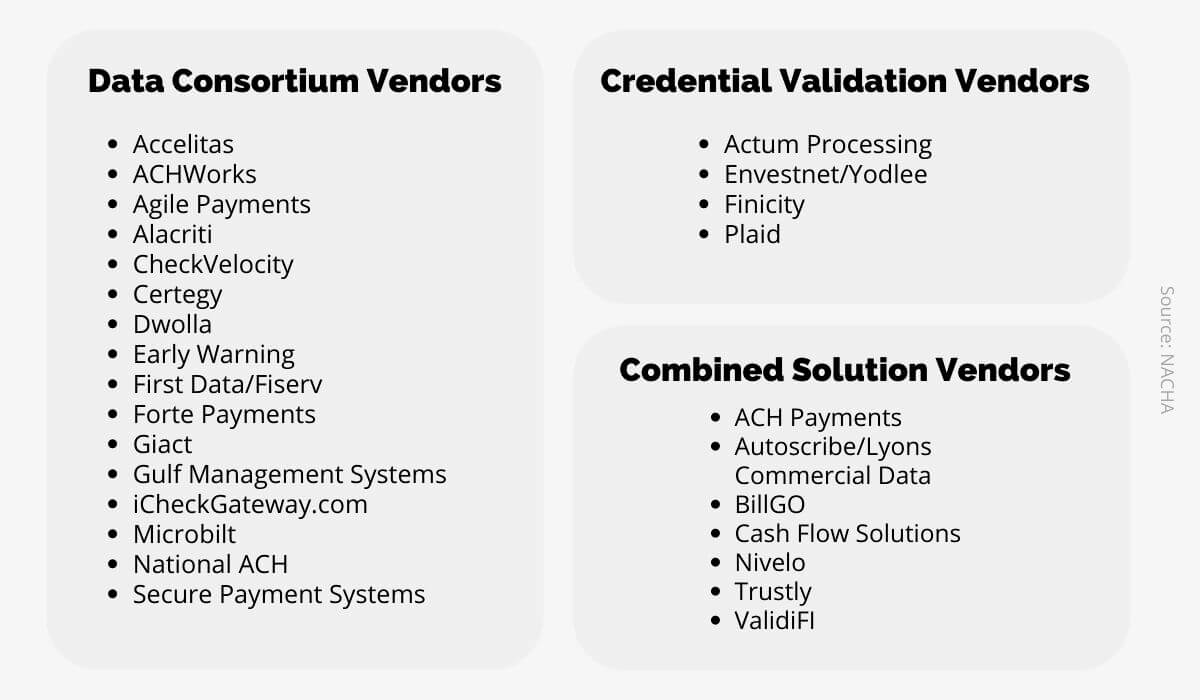
Source: Regpack
Because you need to verify your customers’ identities before processing any online or telephone ACH transactions, it is crucial to choose a payment processing system that includes identity validation.
If the payment processor you use doesn’t offer this service as a part of their process, you’ll need to take independent action to verify customer identities on your own.
In the end, it is your responsibility to make sure you’re following all ACH rules.
Having a dependable know-your-customer policy in place may feel like overkill in this age of global customer bases, but identity verification is crucial for safe transactions and, consequently, consumer satisfaction.
Detecting Fraud
The popularity of ACH billing is rising—in fact, ACH transactions increased by 8.2% in volume and 10.8% in value from 2019 to 2020 alone.
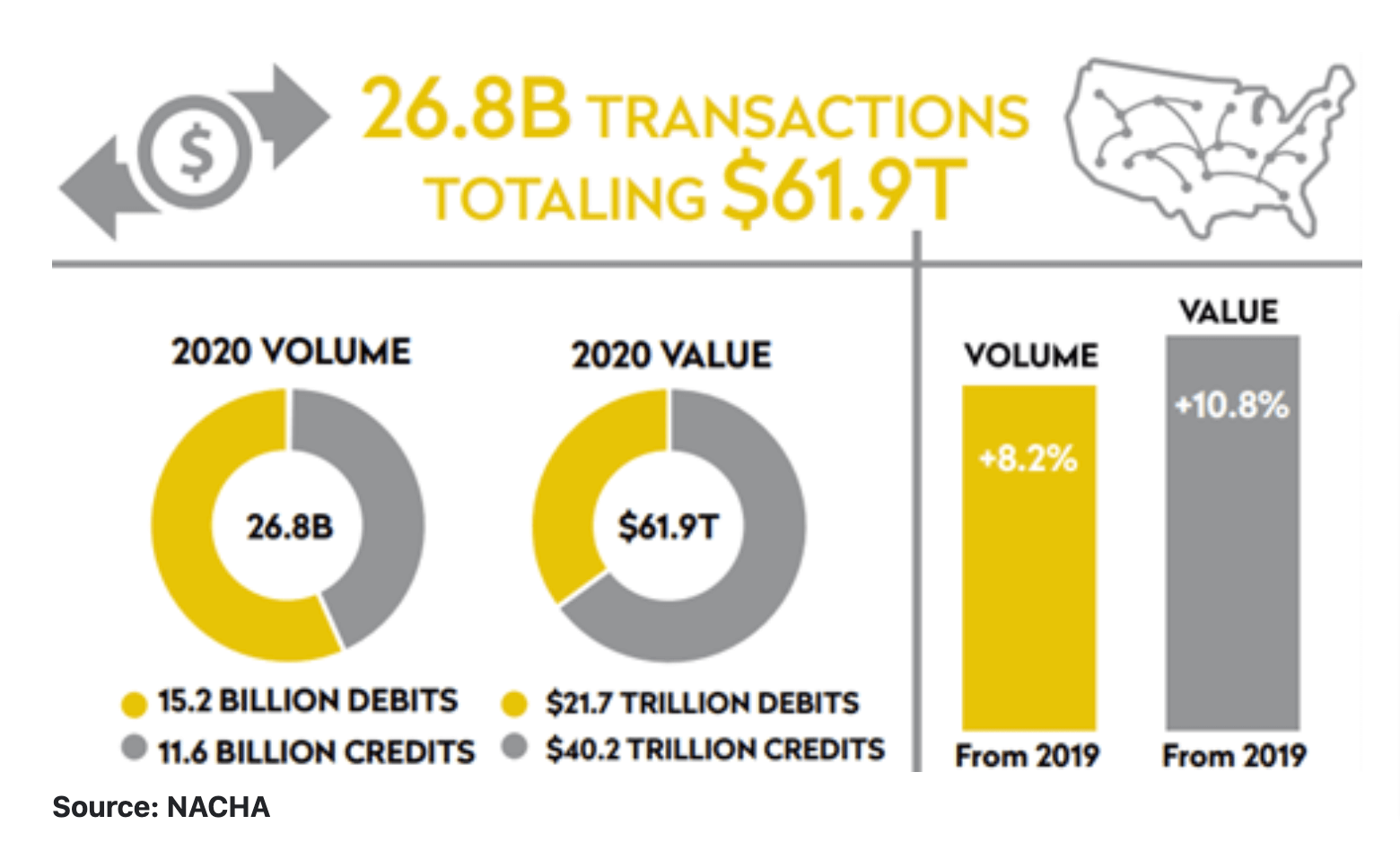
Source: FICO
However, with that increase in usage comes a natural increase in the likelihood of fraudulent attempts.
Even though ACH payments are more secure than many other methods of payment, they’re not completely protected from determined scammers. In fact, the FTC received 2.2 million fraud reports from consumers in 2020.
In light of this reality, Nacha requires merchants and third-party payment processors to identify fraudulent online transactions before they are sent to the ACH network.
Because it’s your responsibility to detect ACH fraud on your end before the payment is sent into the ACH network, you should take special care before choosing a payment processing system.
The platform you choose should have a fraud detection system in place to monitor for duplicate transactions and other suspicious activity.
There are also third-party fraud detection services such as Verafin and Sift available that use specially-designed algorithms to identify fraud within ACH processing.
Creating a Strong Written Security Policy
Finally, the ACH rules require that merchants draw up a written security policy to outline the processes and systems involved in handling their customers’ data.
The security policy should outline how your business acts to prevent fraud and protect your customers’ information.
Thankfully, the requirements for securing your customers’ protected information are similar to the process in place to protect credit card data under the PCI DSS.
So if your business is already PCI-compliant, you likely don’t need to add much more to your written policy besides the following:
- State that bank account information should be treated the same way as cardholder information
- Explain your identity validation process for both online and phone ACH payments
If your business isn’t already PCI-compliant, you’ll need to write a set of security policies that complies with Nacha regulations. You’ll need to address your encryption process, paper and digital file security, internal user permissions, and identity validation procedures.
How Nacha Enforces Security Standards
Typically, ACH security violations are reported to Nacha by the sending or receiving bank. Once Nacha receives an allegation of a security violation, they reach out to the involved parties directly to try to resolve the problem.
Usually, ACH Operating Rule violations don’t result in a penalty; instead, the involved parties work together to resolve the issue once Nacha gets involved. But sometimes, when Nacha’s communications are ignored, the case needs to be escalated.
According to Lorie Nash, Nacha Senior Director of Compliance:

Source: Regpack
The Rules Enforcement Panel is made up of members from ACH Operators and Payments Associations as well as from financial institutions.
The panel hears the case—presented by Nacha—and makes a final decision on whether a violation has taken place. If that’s the case, the violator receives a fine.
ACH Security Summary
Just like PCI DSS for credit card transactions, the ACH Operating Rules set forth by Nacha help ensure that bank payments are as safe and secure as possible.
Whether you’re a small or a large business, if you accept ACH payments, it’s your responsibility to keep your customers’ protected information secure and keep data transmission safe.
Before sending a payment through the ACH network for processing, you’ll need to check for the routing number’s validity, confirm your customer’s identity, and use commercially reasonable practices to detect potential fraud.
And you’ll also need a strong and clear written security policy that outlines your processes and methods for keeping customer data safe and ACH transactions compliant.
For many, accepting ACH payments while remaining in compliance with Nacha guidelines can be intimidating.
One way to take some of the burden off of your shoulders is to work with a secure payment processing system like Regpack. To find out if we’re a good fit for your business, request a free demo today.